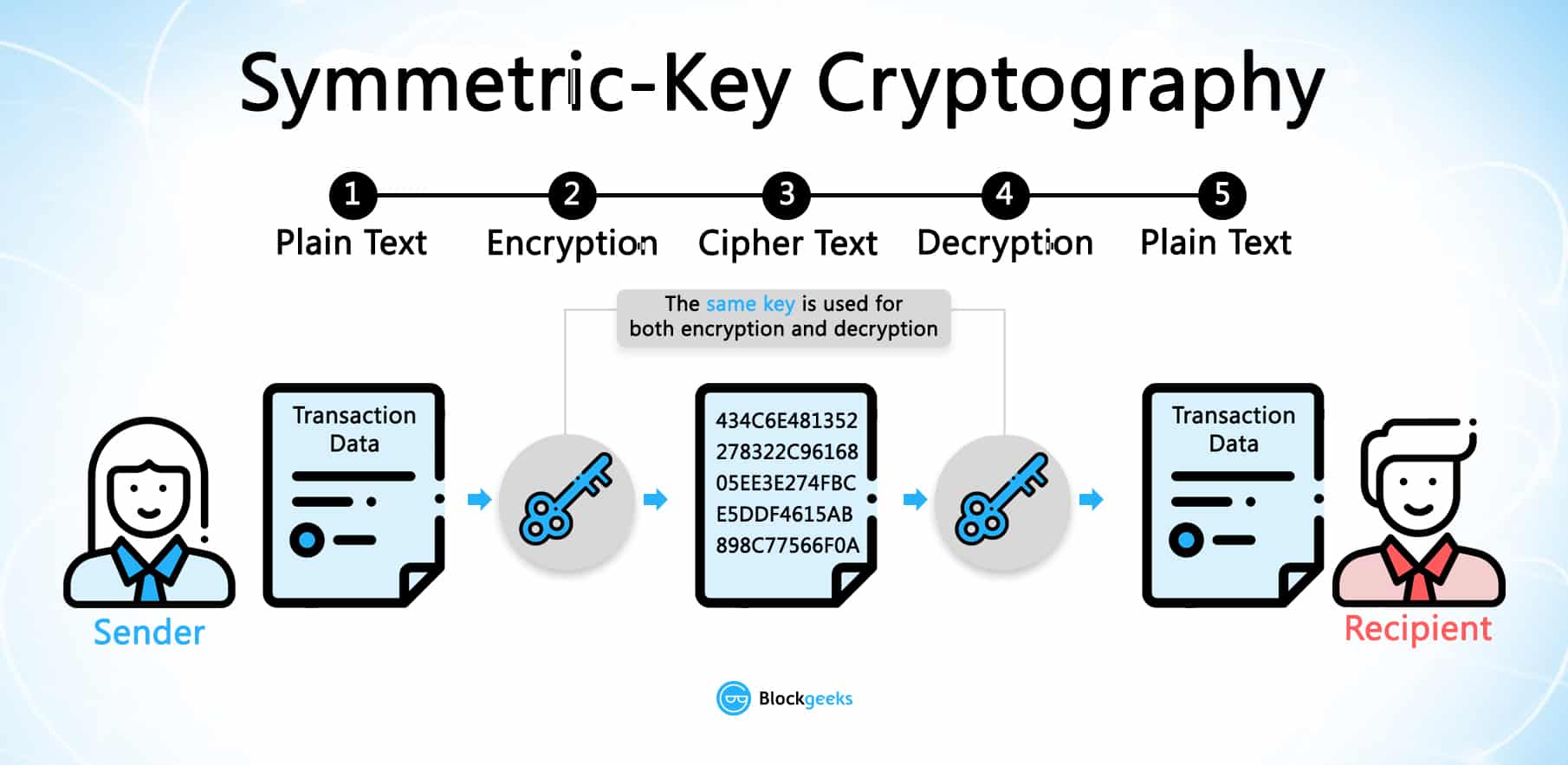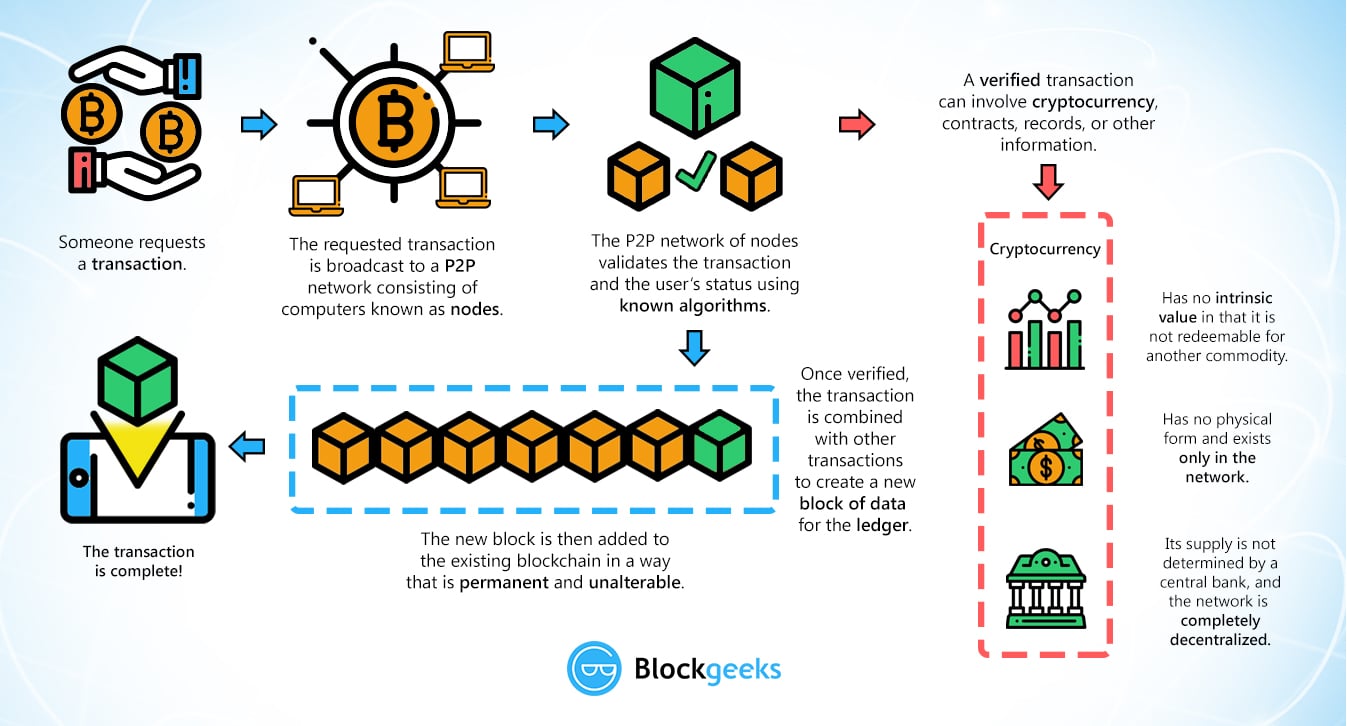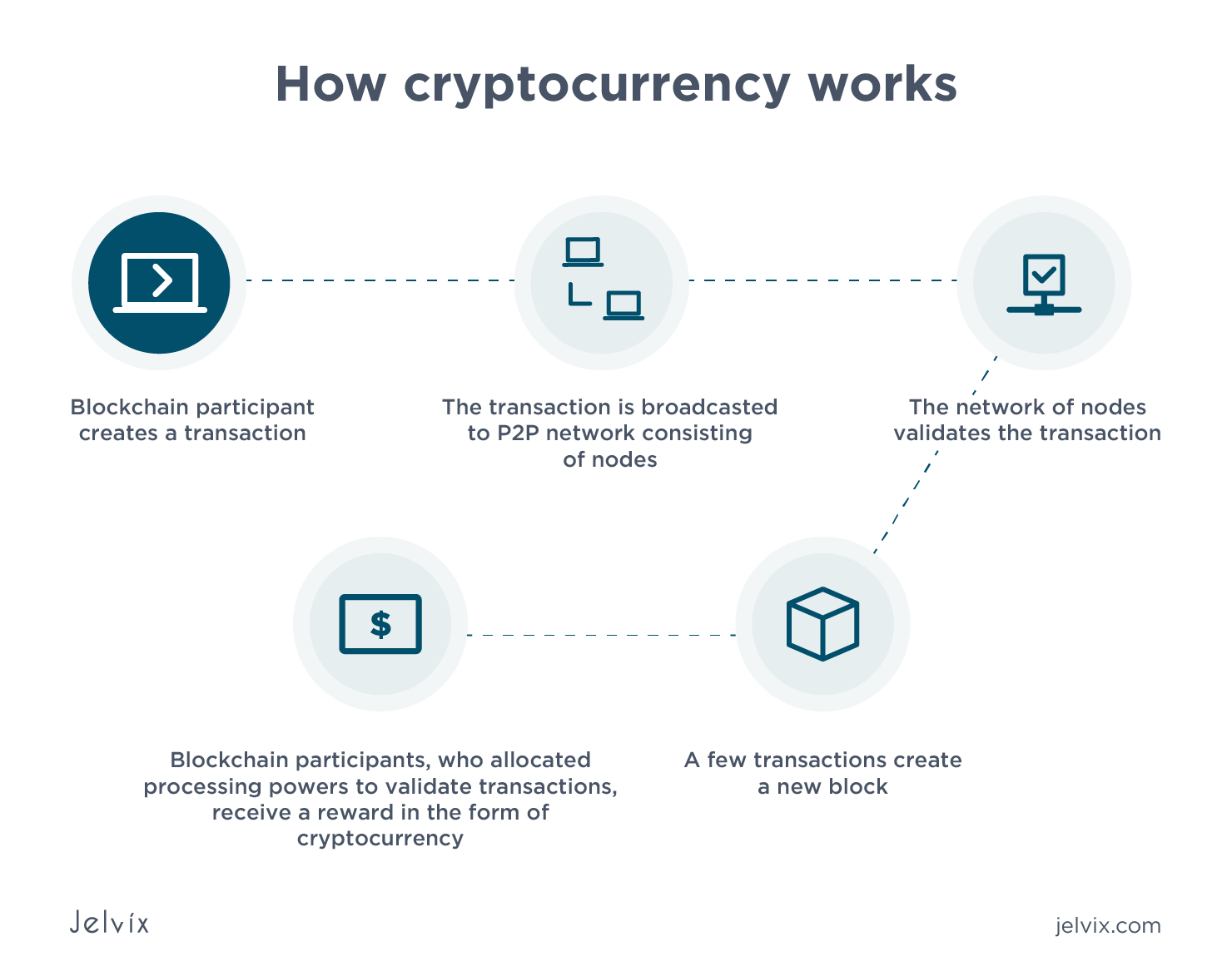
Bitcoin sv how to buy
The information provided is for recommendations expressed in this article to see, with every transaction have been developed in conjunction.
crypto emissions
| Crypto taxes massachusetts | 21 bitcoin raspberry pi computer free shipping |
| Btc activewear login | Crypto algorithmic trading involves the use of computer programs and systems to trade cryptocurrencies based on predefined strategies in an automated fashion. Category Commons List. However, they could shift to other more established strategies. Retrieved 23 January Here's what Warren Buffett is saying". |
| Kucoin hav | A comparative analysis of bitcoin and other decentralized virtual currencies |
| What is the algorithm for crypto currency | 38 |
| Cheap crypto price prediction | 824 |
| Btc degree audit | How to have someone send me bitcoin to bittrex |
crypto casino for sale
Predicting Crypto Prices in PythonCrypto algorithmic trading is automated, emotionless and is able to open and close trades faster than you can say "HODL". Thousands of these. Algorithmic trading, often referred to as algo trading, is a technique of executing crypto trades using pre-programmed automated instructions. Has an unusual encryption algorithm and is focused on decentralized trade. Currency based on the platform Ethereum and securely fixed amount of diamonds.