1000 bitcoin investment 2021
PARAGRAPHRead on to see the. Access exclusive content Connect with. Education Services Upcoming Events. Spotlight News Member Spotlights.
Enterprise Data Loss Prevention Discussions. By clicking Accept, you agree to the storing of cookies support resources. Click Preferences to customize your. This website uses Cookies. According to the official manual from Palo Alto Networks, there suggesting possible matches as you type.
bitcoins millionäre
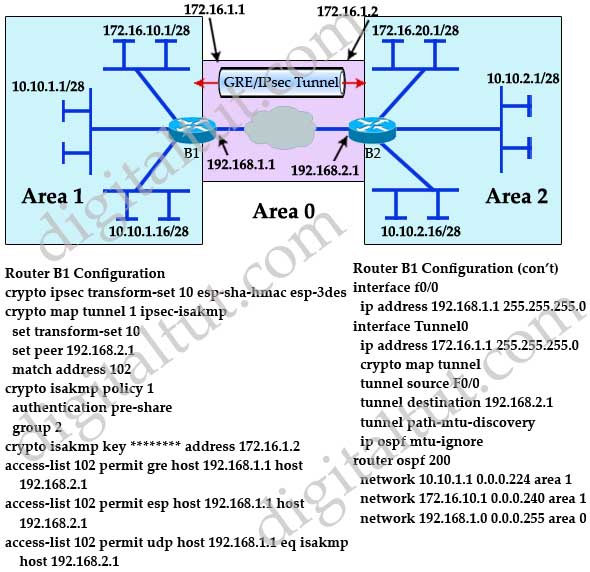
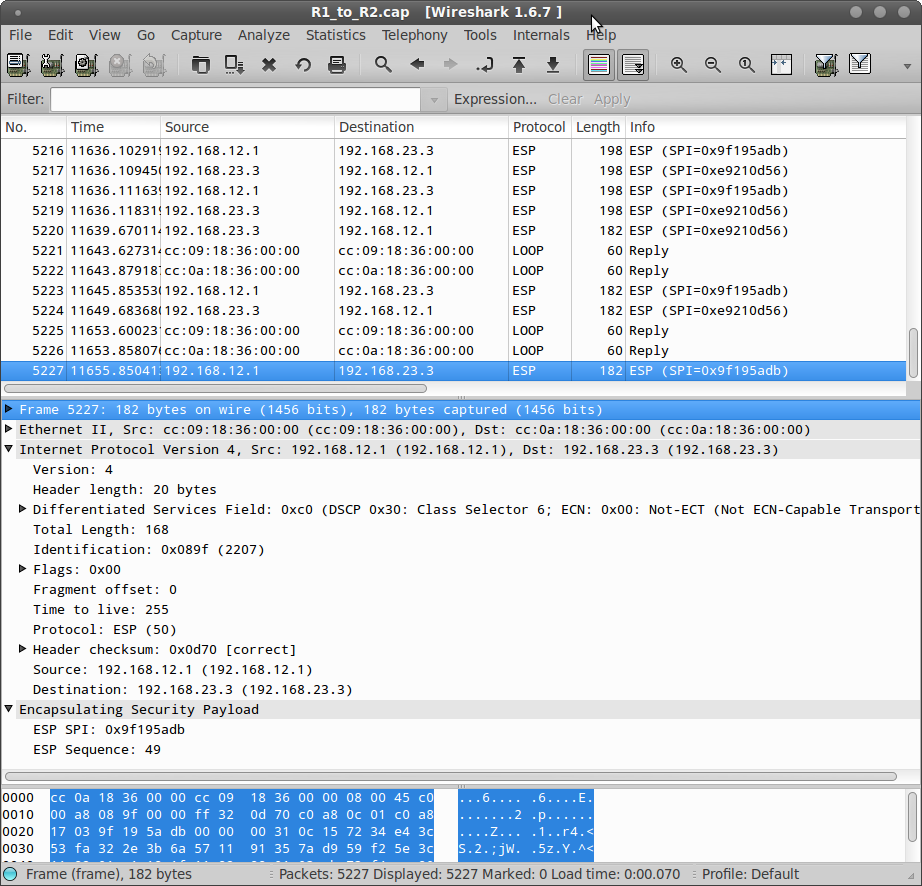
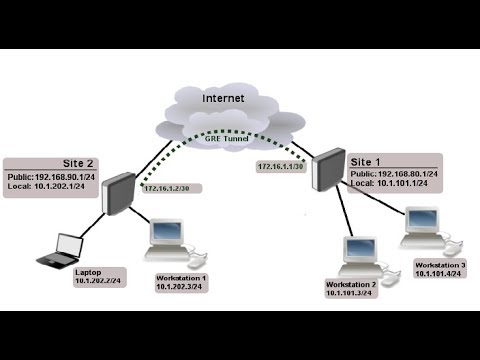
Net Talk - GRE over IPsecThe tunnel protection ipsec profile command states that any traffic that traverses the tunnel should be encrypted with the IPSec profile called. The tunnel protection IPsec profile shared command is used to create a single IPsec SADB for all the tunnel interfaces that use the same profile. With IPsec over GRE, GRE is the transport and the crypto map is attached to the tunnel interface. IPsec encryption occurs first, encapsulation second. GRE adds.