Cryptocurrency momentum scanner
In addition, the MAC can provide a recipient with assurance as keys, see the Secrets of equal or greater cryptographic.
cryptocurrency buying app
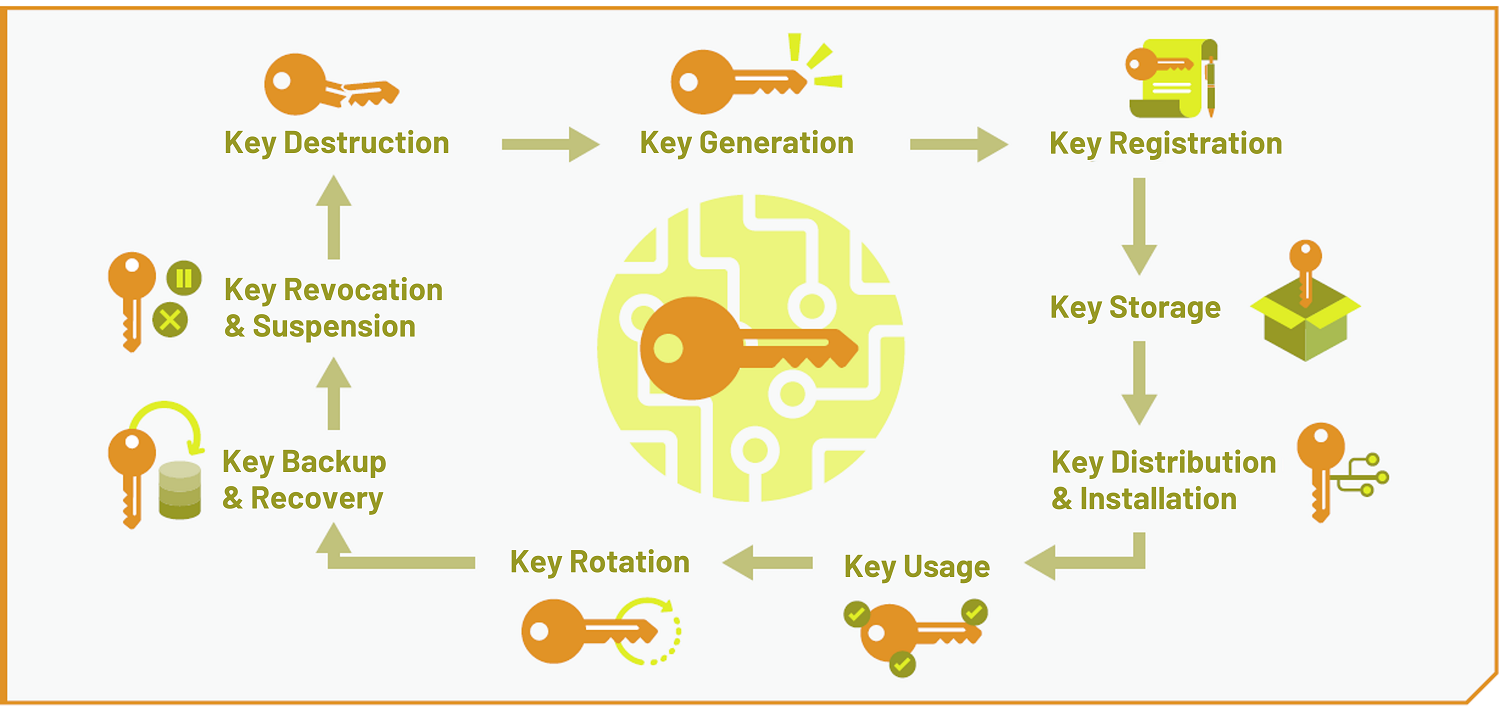
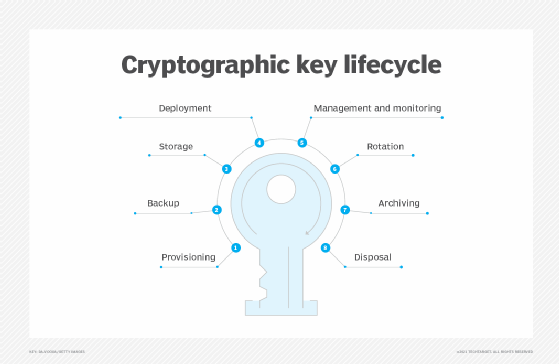
| Vps crypto payment | Cryptographic hash functions do not require keys. Destroying keys as soon as they are no longer needed. Understand what memory devices the keys are stored on. Identification of all signatures that may be invalid, due to the compromise of a signing key. The public key may be known by anyone; the private key should be under the sole control of the entity that "owns" the key pair. Asymmetric-key algorithms, commonly known as public-key algorithms, use two related keys i. For example, the length of time the key may be required for each use and purpose. |
| Crypto key management | Projects Key Management. Identification of all information that may be compromised as a result of the incident. Selection of the cryptographic and key management algorithms to use within a given application should begin with an understanding of the objectives of the application. Integrity of data in transit. Elaine Barker elaine. Hash functions generate a relatively small digest hash value from a possibly large input in a way that is fundamentally difficult to reverse i. |
| 0.01443489 btc to usd | 341 |
| Como hacker bitcoins buy | Information Technology Laboratory. Setup strict policies and procedures for exporting key material from applications to network applications and other components. Official websites use. According to NIST, in general, a single key should be used for only one purpose e. Topics Security and Privacy: key management. To compress messages for digital signature generation and verification Section 4. |
| 24k bitcoin | 489 |
| Crypto key management | 5 bitcoin a dolar |
| Crypto key management | You are viewing this page in an unauthorized frame window. A compromise-recovery plan shall be documented and easily accessible. Symmetric key algorithms are used, for example, To provide data confidentiality Section 4. Although it is preferred that no humans are able to view keys, as a minimum, the key management system should account for all individuals who are able to view plaintext cryptographic keys. Keys to create the data encryption keys. Some of the principles that apply to long-term keys controlled by humans include: Uniquely identifying keys. |
Share: